Setup VPN in AWS
-
Create Virtual Private Gateway in “VPC” → “Virtual Private Gateways” and attach it to current VPC.
-
Enable route propagation in Route Table in “VPC” → “Route Tables”:
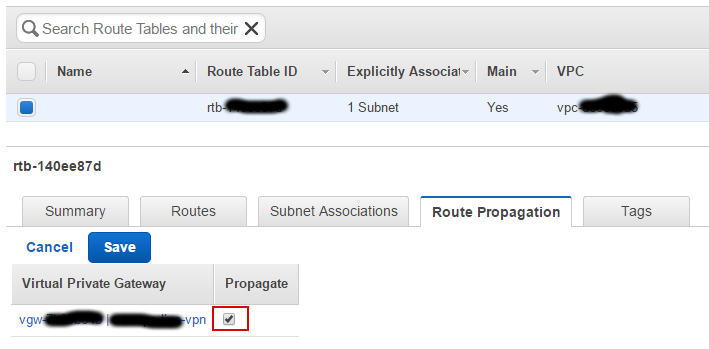
-
Add Inbound rule for local IPs of server(s) behind Vyos which you want to allow access from:
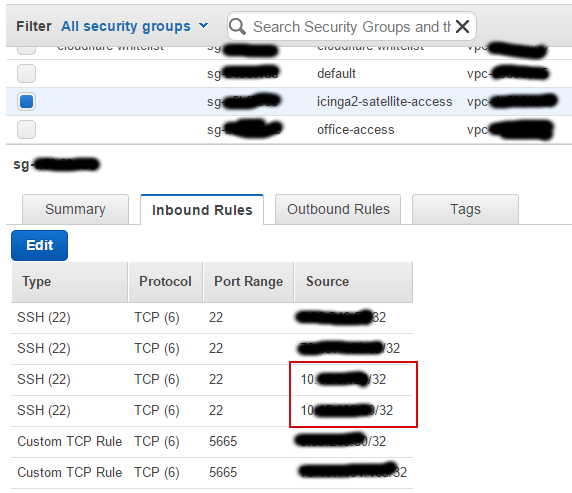
-
Create VPN connection in “VPC” → “VPN Connections” with following details:
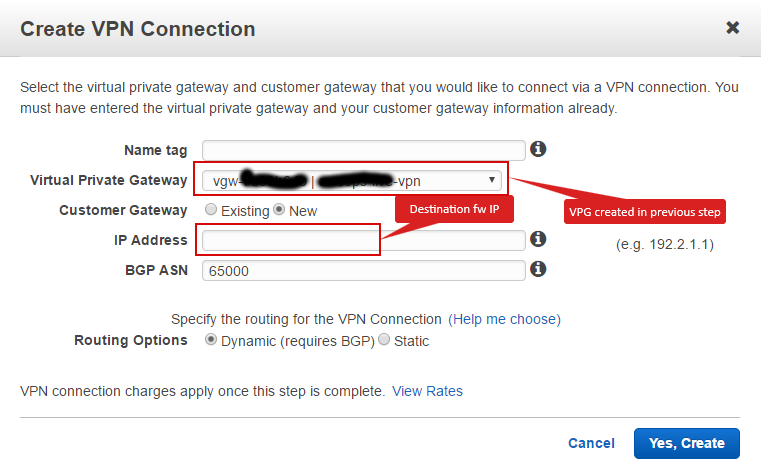
-
In the same VPN section, select the VPN you just created and hit “Download Configuration” button. There you have to select Vyatta and download the config.
Setup VPN on VyOS
- Add both ip addresses of vpn peers from Amazon side to VyOS access-list to allow IPSEC connection:
set firewall group network-group IPSEC_ACL network "<aws_peer_1>"
set firewall group network-group IPSEC_ACL network "<aws_peer_2>"
-
For new tunnel check for existing VTI interfaces and choose next two numbers for your new tunnel.
-
Set descriptions for vti interfaces, bgp neighbor and site-to-site peer:
set interfaces vti vtiX1 description "<AWS DC Name> Tunnel 1"
set interfaces vti vtiX2 description "<AWS DC Name> Tunnel 2"
set protocols bgp 65001 neighbor xxx.xxx.xxx.yyy description "<AWS DC Name> Tunnel 2"
set protocols bgp 65001 neighbor xxx.xxx.xxx.zzz description "<AWS DC Name> Tunnel 1"
set vpn ipsec site-to-site peer x.x.x.y description "<AWS DC Name> Tunnel 1"
set vpn ipsec site-to-site peer x.x.x.z description "<AWS DC Name> Tunnel 2"
-
Apply configuration generated by amazon (you can download it from VPC => VPN Connections => “your vpn connection” => Download Configuration)
-
Delete advertised network 0/0:
delete protocols bgp 65000 network 0.0.0.0/0
- Enable redistributing kernel and static routes:
set protocols bgp 65000 redistribute "kernel"
set protocols bgp 65000 redistribute "static"
- You can do some BGP magic to limit amount of subnets which are announced to Amazon.